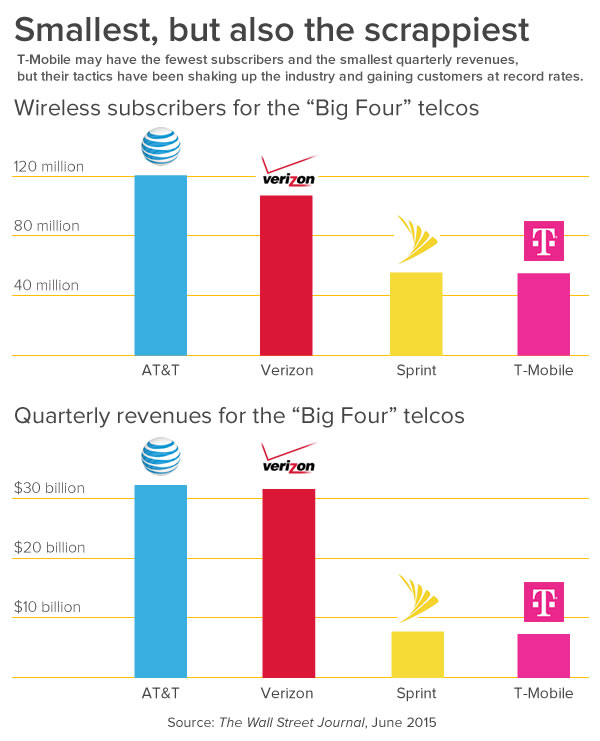
The case of
Rajaee v. Design Tech Homes, Ltd.

In 2012, Saman Rajaee started work as a Houston-area salesman for Design Tech Homes, a Texas-based house-building firm. Design Tech didn’t provide mobile phones for their workers, and asked them to use their personal devices instead.
Rajaee used his iPhone 4 not only for work-related voice calls, but for work-related email as well. That meant connecting his iPhone to Design Tech’s Microsoft Exchange Server. Doing so requires an exchange (if you’ll forgive the pun) of privileges; in exchange for access to company resources from your mobile device, the server is granted the ability to enforce security policies on that device. One of those policies is remote wipe, which allows the server to completely erase the contents of a mobile device connected to it, and restoring it to its original factory “fresh out of the box” settings.
At the start of February 2013, Rajaee gave Design Tech his two weeks’ notice, and Design Tech immediately terminated him. A few days later, Design Tech’s system administrator issued the remote wipe command to Rajaee’s iPhone, which erased everything on it, both work-related and personal.

Rajaee sued Design Tech, claiming that what they did caused him to lose contact information for hundreds of business contacts and family (much of whom lived overseas), business information, passwords, and irreplaceable personal data, including family photos and videos. He said in performing the remote wipe, Design Tech violated the Electronic Communications Privacy Act, the Computer Fraud and Abuse Act and Texas Theft Liability Act. In response, Design Tech filed a motion requesting a summary judgement.
The case was decided in Texas Federal Court, and Design Tech was able to get the case dismissed in November 2014. Their victory was based on these points:
- A holding from the 5th U.S. Circuit Court of Appeals says that information that an individual stores on a hard drive or mobile device isn’t considered to be in electronic storage according to the definition of the term in the Electronic Communications Privacy Act (ECPA). The court determined that the personal data stored on Rajaee’s iPhone was not legally protected and hence his claim under the ECPA was dismissed.
- To be considered a violation of the Computer Fraud and Abuse Act (CFAA), Rajaee needed to prove that the remote wipe caused him a loss of at least $5,000. Rajaee said that the personal photos, videos, and messages were worth more than that, but Design Tech’s lawyers were able to establish that Rajaee just couldn’t demonstrate that the loss of that data was worth $5,000 or more, nor was he able to show any evidence of costs incurred to investigate or respond to the remote wipe, which led to his claim under the CFAA also being dismissed.
- The last leg of Rajaee’s case, the Texas Theft Liability Act, vanished since the court was a federal one and the law is a state law. The court declined to, in legalese, “declined to exercise supplemental jurisdiction over the remaining state law claims.”

The only people who walked away happy from the case were the lawyers. Rajaee lost irreplaceable data and mementoes, not to mention time doing whatever re-setting up he had to do on his iPhone, and both parties spent time and money on the case, with Design Tech spending a lot of money on a big-name law firm.
What both sides did wrong

Rajaee’s biggest mistake is one that a lot of us make: failing to back up his phone. Even in those long-ago days of 2013 — that’s almost 10 internet years ago! — backing up an iPhone was pretty much an automatic process, either via services like iCloud, or plugging into your computer and backing it up through software like iTunes, which can be set up to do so automatically as soon as you hook up the USB cable. In a world where precious memories like personal photos and videos are digital and hard drive and cloud storage space is cheap and plentiful, you’re a fool if the one and only place they live is your phone.
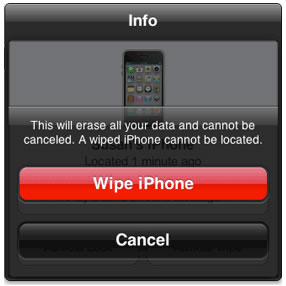
Design Tech made a couple of mistakes. The first one was performing the remote wipe. Remote wipes are the nuclear option of mobile security. They’re meant to be used if and only if the phone is believed to be irretrievably lost, in which case it’s a security risk since it has access to corporate resources. Design Tech’s system administrator could’ve simply revoked Rajaee’s iPhone’s access to the Exchange server, which would simply make the Design Tech email messages, contacts, and calendar access disappear, without affecting or altering any of the phone’s other settings. Given that Design Tech’s response to Rajaee giving them two weeks’ notice was to terminate him immediately, it’s not hard to imagine them giving their sysadmin the order to issue the remote wipe command out of spite.
Design Tech’s second mistake was not having a mobile policy that its employees and contractors could agree to and sign.
Having a BYOD (Bring Your Own Device) policy is the best policy

If your organization is going to allow employees to use personal mobile devices for work — that’s smartphones, tablets, and any other portable device that runs what’s considered to be a mobile operation system (Android, iOS, or Windows Phone, to cite a few examples) — you’ll need to:
- First consider how you’d want employees to use their personal devices for work. Will they simply be taking voice calls? Accessing corporate email, contacts, calendar, or some combination of the three?
- Write down those ways you’d want employees to use their personal devices at work in a BYOD policy. Spell out what is and isn’t acceptable use. State that when an employee connects his/her device to the corporate network and/or using it for company business, that s/he is granting access to the device to the organization.
- Spell out the conditions that would necessitate revoking the device’s access to the corporate network. Spell out the conditions that would necessitate a remote wipe. If you don’t want to be a jerk, make it so that the conditions for a remote wipe are something akin to the device being irretrievably lost.
- Educate employees about the BYOD policy, and make those who want to use their personal devices at work sign it.
- Document everything: the policy itself, the processes and technology that enforces it, and the education process. Keep the signed policies in your records.
By having a BYOD policy, you can avoid the risk of a Rajaee v. Design tech Homes, Ltd. situation and save a lot of money, headaches, and your reputation.
If you need more convincing, take a look at our white paper titled No More Excuses: Why Your Business Needs a Mobile Policy. It looks at the most common excuses for not having one, which run the gamut from “I don’t know what to include in a policy” to “It’s an HR thing” to “We have BYOD”, and explains why they don’t let you off the hook. You’ll also get some first steps that you should take once you’ve said “no more excuses!”