In 2012, I wrote an article about Pyramid Research’s predictions for the smartphone market in 2015.
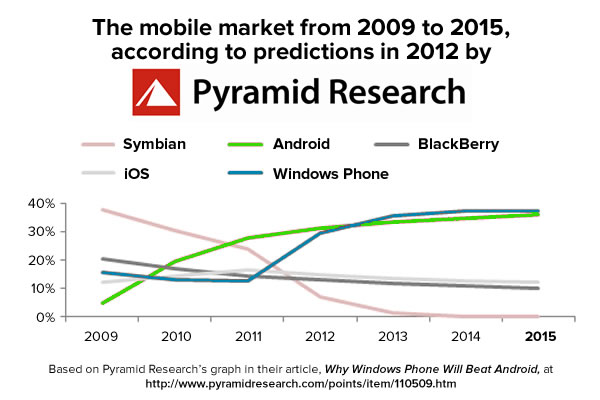
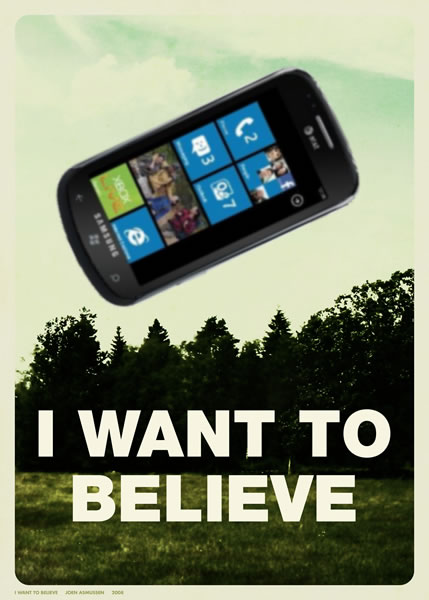
Since then, I’ve been waiting for the first day of this magic year to write this blog post. That’s because back in 2011, mere days after leaving my roles in Microsoft Canada as a Developer Evangelist and Windows Phone Champ, Pyramid Research said that in 2015, Windows Phone would edge out Android to become the most-used mobile OS in the world, with nearly 40% of the market share:
Click the graph to read the article it was derived from.
Here’s what they wrote (with emphasis added by Yours Truly):
Now, a couple of words about the “controversial” projection itself. While we acknowledge the momentum that Android is experiencing and will continue to experience in 2011 and 2012, we believe that Nokia and Microsoft are a very powerful tandem, and that will show in its full force by the end of 2013. Some of the main obstacles to the growth of WP to date will be removed, as Nokia helps with bringing down the price of WP smartphones. Lower price of the devices will be the crucial prerequisite for the expansion of WP models.Nokia knows it and Microsoft knows it, and I am sure they will act on it quickly. It’s also worth mentioning that, apart from Nokia, quite a few other large handsets vendors in the world, such as Samsung, LG and Sony Ericsson are still placing their bets on WP. With the change in the price of WP devices, and the multivendor strategic approach of Microsoft, the main advantage of Android – scale – may be removed.
And although Nokia has suffered a significant loss from dragging out the Symbian story for too long, it’s Nokia we are talking about: They are big enough and strong enough to take on a couple of painful hits and come out of the struggle stronger than ever. They are in a good position to learn and adjust because they know what was bad about Symbian, what’s creating gains and what’s causing problems for Android, as well as what the upsides and downsides of a system such as that of Apple, where the OS only runs on hardware manufactured by the vendor.
Don’t forget that while being late to the party is rude, everybody gets to see you enter the room. When Nokia “enters the room” with new WP-based devices, there will likely be much traction about its new “clothes and shoes,” which will be a good jump start for the new era of WP devices.
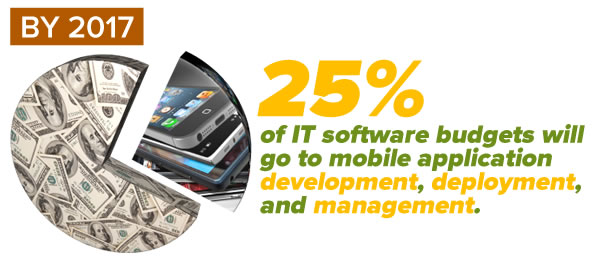
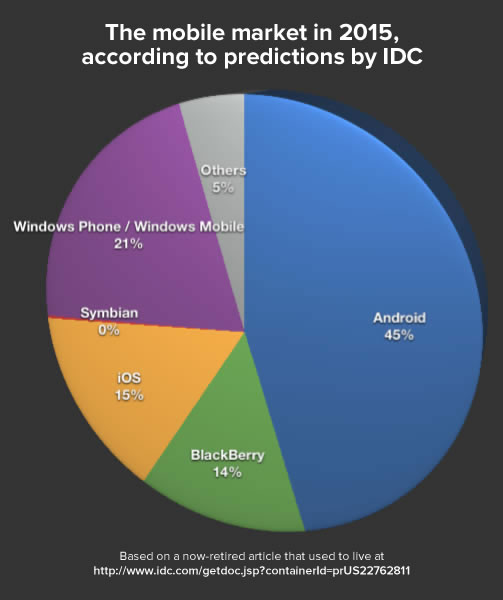
IDC’s predictions for the 2015 mobile market weren’t quite so wacky. They predicted that Windows Phone wouldn’t claim the top spot, but be the runner-up OS, with 21% of the market:
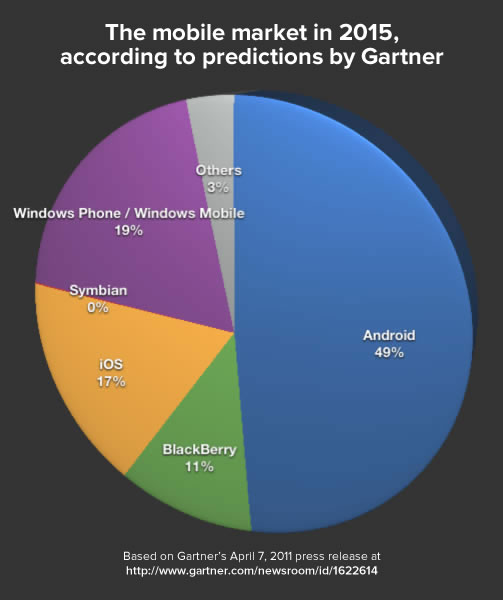
Gartner’s predictions were the least deluded. They predicted that Windows Phone and iOS would be roughly tied for second place, each with about a fifth of the mobile OS market:
Click the graph to read the press release it was derived from.
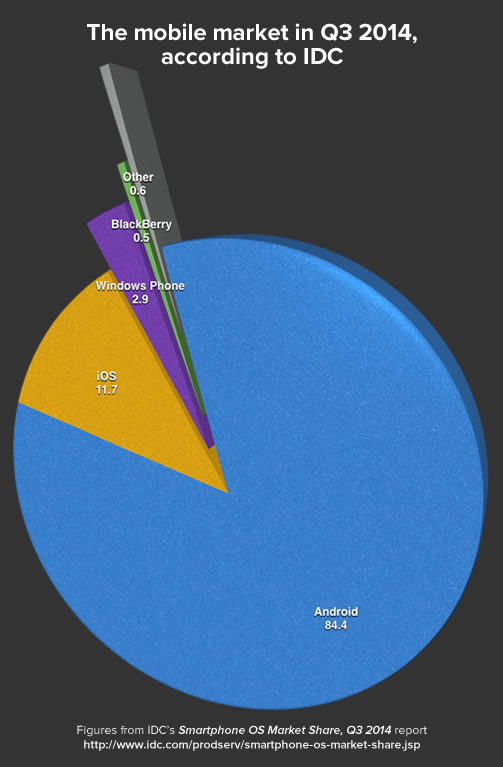
In case you weren’t sure how the mobile OS market share story turned out, here’s a graph made from data from IDC’s Smartphone OS Market Share, Q3 2014 report:
Click the graph to read the report it was derived from.
It’s tough to make predictions, especially about the future, and let’s face it, I rely on data from analyst firms like Gartner and IDC in my line of work, but I do take everything they say with the appropriately-sized grain of salt. (I’m still a bit leery about Pyramid Research.) Over the past decade, the world of mobile has given us so many surprises and thrown us so many curve balls that it’s tough enough trying to predict what’ll come in the next year, never mind the next two or five.
And hey, there’s always a chance that Microsoft will rally and somehow grow Windows Phone’s share six over seven times over the next 364 days.