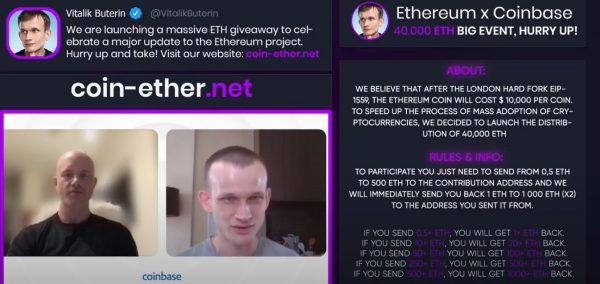
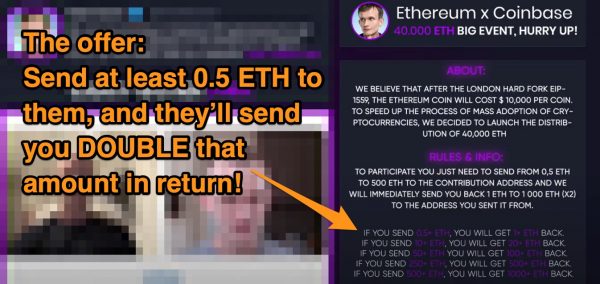
Here’s your weekly list of tech, entrepreneur, and nerd events — plus a little area tech news — for Tampa Bay and surrounding areas for the week of Monday, November 8 through Sunday, November 14, 2021.
This is a weekly service from Tampa Bay’s tech blog, Global Nerdy! For the past four years, I’ve been compiling a list of tech, entrepreneur, and nerd events happening in Tampa Bay and surrounding areas. There’s a lot going on in our scene here in “The Other Bay Area, on the Other West Coast”!
As far as event types go, this list casts a rather wide net. It includes events that would be of interest to techies, nerds, and entrepreneurs. It includes (but isn’t limited to) events that fall under the category of:
- Programming, DevOps, systems administration, and testing
- Tech project management / agile processes
- Video, board, and role-playing games
- Book, philosophy, and discussion clubs
- Tech, business, and entrepreneur networking events
- Toastmasters (because nerds really need to up their presentation game)
- Sci-fi, fantasy, and other genre fandoms
- Anything I deem geeky
By “Tampa Bay and surrounding areas”, this list covers events that originate or are aimed at the area within 100 miles of the Port of Tampa. At the very least, that includes the cities of Tampa, St. Petersburg, and Clearwater, but as far north as Ocala, as far south as Fort Myers, and includes Orlando and its surrounding cities.
This week’s events
This list includes in-person events as well as online events. The COVID-19 numbers are dropping sharply, but be smart and responsible — get your shots, mask up in crowds, and we can get back to what passes for normal sooner!
I try to keep this list up-to-date. I add new events as soon as I hear about them, so be sure to check this page often!
Monday, November 8
| Coachieve | Entrepreneur Crash Course – Tampa | |
| Tampa Bay Tech Career Advice Forum | Job Seeker Coffee Talk | 9:00 AM |
| Tampa Bay Times | Tampa Bay Job & Career Fair | 10:00 AM to 2:00 PM EST |
| Entrepreneurs with ADHD | Monday Kick Off (avail. Online) | 11:00 AM |
| Wesley Chapel, Trinity, New Tampa Business Professionals | Lutz, Wesley Chapel, New Tampa Virtual Networking Lunch | 11:30 AM |
| Professional Business Networking with RGAnetwork.net | Tampa Bay Virtual Networking Lunch Monday & Wednesday All Welcome JOIN us | 11:30 AM |
| Tampa / St Pete Business Connections | South Tampa Professional Networking Lunch | 11:30 AM |
| Young Professionals of Tampa Bay Networking Group | South Tampa Referrals | 11:30 AM |
| Christian Professionals Network Tampa Bay | Live Online Connection Meeting- Monday | 11:30 AM |
| Entrepreneurs & Business Owners of Sarasota & Bradenton | Virtual Networking Lunch Monday & Wednesday | 11:30 AM |
| Thinkful Tampa | Thinkful Webinar || Intro to Data Analytics: SQL Fundamentals | 12:00 PM to 1:30 PM EST |
| Tampa Bay WaVE | CyberTech|X Accelerator “Ask Me Anything” Session | 1:00 PM |
| West Orange Comics & Video Games | Magic Mondays | 5:00 PM |
| Airbnb Hosts of Tampa | Airbnb Host Meetup | 5:00 PM |
| Tampa Tabletop | Monday Feast & Game Night | 6:00 PM |
| Toastmasters Division G | Radiant Ridge Toastmasters | 6:00 PM |
| Board Game Meetup: Board Game Boxcar | Weekly Game Night! (Lazy Moon Location) | 6:00 PM |
| Professional South Tampa Ladies | Ladies Night at Shooter’s World | 6:00 PM |
| Lakeland Black Professionals | LBP Nov Virtual Meeting | 6:00 PM |
| Critical Hit Games | MTG: Commander Open Play | 6:00 PM |
| Tampa Bay Gaming: RPG’s, Board Games & more! | MTG: Commander Open Play (At Critical Hit Games) | 6:00 PM |
| Magic the Gathering Tampa/Brandon/St Pete | Commander Night | 6:00 PM |
| Thoughtful Writing | Philosophy in Writing | 6:00 PM |
| Beginning Web Development | Weekly Learning Session | 6:00 PM |
| Tampa – Sarasota – Venice Trivia & Quiz Meetup | Trivia Night – Off the Wagon Kitchen & Brewery Smartphone Trivia Game Show | 6:30 PM |
| Toastmasters District 48 | Cool, Confident & Politically Imperfect Toastmasters | 6:45 PM |
| Orlando Stoics | ONLINE: The 71 Golden Verses of Pythagoras | 7:00 PM |
| South Florida Poker, Music & Entertainment Group | FREE Texas Holdem Poker Tournaments at Fireside Lounge & Billiards 7 PM Start | 7:00 PM |
| Library Book Clubs – OCLS | Virtual Event: Southeast Book Club | 7:00 PM |
| Brandon WordPress Meetup | TBA: Regular WordPress Meeting | 7:00 PM |
| Learn-To-Trade Cryptocurrency (as seen on Orlando Sentinel) | Learn-To-Trade Q&A (0NLINE) | 7:00 PM |
| Nerdbrew Events | Anime Watch Party | 7:00 PM |
| Tampa Hackerspace | Make and Take Kiln Fired Pinch and Coil Pots (Week 4 of 4) | 7:00 PM |
| Central Florida AD&D (1st ed.) Grognards Guild | World of Greyhawk: 1E One-Shots | 7:30 PM |
| Thinkful Tampa | Thinkful Webinar | UX/UI Design Vs. Web Development | 8:00 PM to 9:30 PM EST |
| Thinkful Tampa | Careers in Tech | Thinkful Webinar | UX/UI Design Vs. Web Development | 8:00 PM |
Tuesday, November 9
Wednesday, November 10
Thursday, November 11
Friday, November 12
Saturday, November 13
Sunday, November 14
| Thinkful Tampa | Thinkful Webinar || Intro to HTML & CSS: Build Your Own Website | 9:00 AM to 10:30 AM EST |
| Saint Petersburg Introverts Socializing (Ages 25-40) | Yoga and Group Meditation | 9:00 AM |
| Geekocracy! | Return of the Geeks to the zoo | 9:30 AM |
| Thinkful Tampa | Thinkful Webinar || Learn Data Analytics With Thinkful | 12:00 PM to 1:30 PM EST |
| ITADAKIMASU Tampa Japanese Food Meetup | Oden – SUNDAY | 12:00 PM |
| Board Games and Card Games in Sarasota & Bradenton | Games at Table Talk SRQ | 12:00 PM |
| Meeple Movers Gaming Group | Game Night at The Juniper General Store | 3:00 PM |
| Nerd Night Out | Taps and Drafts | Innistrad: Crimson Vow Pre-Release | 4:00 PM |
| Tampa Stoics | IN-PERSON: A Walking Meditation – Causeway Trail | 5:00 PM |
| Tampa Hackerspace | Sew Awesome! (Textile Arts & Crafts) | 5:30 PM |
| Thinkful Tampa | Thinkful Webinar || UX/UI Design: Creating A Design System | 6:00 PM to 7:30 PM EST |
Do you have any events or announcements that you’d like to see on this list?
Let me know at joey@joeydevilla.com!
Join the mailing list!
If you’d like to get this list in your email inbox every week, enter your email address below. You’ll only be emailed once a week, and the email will contain this list, plus links to any interesting news, upcoming events, and tech articles. Join the Tampa Bay Tech Events list and always be informed of what’s coming up in Tampa Bay!