
This article also appears in The Adventures of Accordion Guy in the 21st Century.
 One of the technologies mentioned in Bruce Sterling’s 1989 novel Islands in the Net (here’s its Wikipedia entry) is the watchphone. Worn like a wristwatch (remember those?), the watchphone was a personal computer that you carried about everywhere and functioned as many things, including timepiece, mobile phone, personal organizer and keys to your house. Today’s smartphones are used in pretty much the same way, and in some cases, in ways that Sterling didn’t anticipate. The two big differences between watchphones and real-world smartphones are:
One of the technologies mentioned in Bruce Sterling’s 1989 novel Islands in the Net (here’s its Wikipedia entry) is the watchphone. Worn like a wristwatch (remember those?), the watchphone was a personal computer that you carried about everywhere and functioned as many things, including timepiece, mobile phone, personal organizer and keys to your house. Today’s smartphones are used in pretty much the same way, and in some cases, in ways that Sterling didn’t anticipate. The two big differences between watchphones and real-world smartphones are:
The New York Times article Tools of Entry, No Need for a Key Chain shows we may be striking that second item from the list above soon:
Right now, using your smartphone as a key isn’t as simple as using an electronic key fob or one of those magnetic keycards that you see dangling from white-collar office workers everywhere. You often have to unlock your phone, launch the app, then press the correct button or buttons to unlock a door. NFC (Near Field Communication) chips, which are starting to appear in smartphones will make it easier to use phones as keys, but it’ll be a couple of years before they’re commonplace.
There are also some issues that we’ll have to deal with in a world where smartphones are keys:
It’ll be interesting figuring this stuff out in the next couple of years.
I’d like to wish my American friends a happy 4th of July! Have a safe and happy holiday, and please enjoy this Independence Day-themed version of everyone’s favourite musical cat meme.
This article also appears in The Adventures of Accordion Guy in the 21st Century.
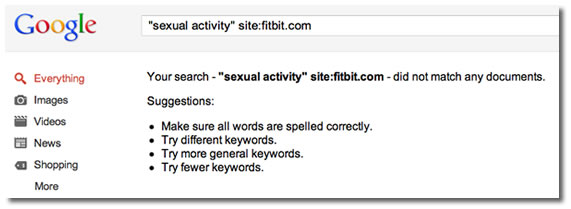
Screen capture of a Google search for Fitbit profiles containing sexual activity.
Don’t bother Googling for "sexual activity" site:fitbit.com anymore. Earlier today, using those search terms would’ve given you the profiles of Fitbit users who were both sharing their activity logs and counting sexual activity as part of their calorie-burning efforts. As of this writing, Google seems to have acted in the interests of privacy by not returning any results for those terms. (Bing, on the other hand, returns ten results as I write this.)

A Fitbit device.
The problem comes from a design decision that probably made sense in the abstract, back when they were designing the software. Fitbit lets you set the privacy levels of various section of your online profile individually. Fitness goals are one section, activities are another. Many people are a bit self-conscious about their weight and naturally set their fitness goals to “private”.
At the same time, many people want to announce to the world that they’re working out. Since that’s not the sort of thing most people are embarrassed about — in fact, it’s something some people like to brag about how often they go to the gym — it’s not too surprising that they set their activity log to “public”.
Finally, there’s the ability to manually enter activity data. Most people won’t wear the Fitbit all the time, but want to count every calorie burned. Manually entering activity data lets you count those activities when you’re Fitbit-free towards your calorie burn. Among those activities is sex, which burns far fewer calories than you’d think.
Combine all these factors and you have situations where your user profile hides your target weight, but shows all those intimate encounters that you faithfully logged — not out of braggadocio but the simple desire to count every last calorie expended. The saving grace is that since Fitbit is a health program, most people’s descriptions of their sexual activity in their Fitbit logs sound rather clinical. Most of the descriptions are more along the lines of “light kissing” and “vigorous activity” rather than “OMG PILEDRIVER” and “What what in the butt”.
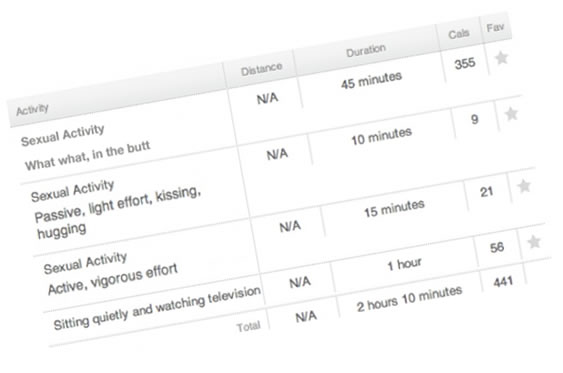
A (slightly doctored) Fitbit activity profile.
For software developers and designers, this is an object lesson in unintended consequences and privacy. The fact that Fitbit gave users control over the privacy settings of various parts of their profile shows that they were designing with their users’ privacy in mind; it’s just that the implementation didn’t account for the fact that some activities may be private. I wonder how they’re going to redesign around that problem.
For users, the lesson is that you should check your online profiles regularly. Just as you look in the mirror before you leave the house (well, some people do), you should make sure that you’re presenting yourself to the online world in the way you want.
This article also appears in The Adventures of Accordion Guy in the 21st Century.
This set of satirical, funny-because-it’s-true org charts for big tech companies has been doing the internet rounds for the past couple of days. (The original version, by Emmanuel “Manu” Cornet, is here.) It shows the chain of command at Amazon, Google, Facebook, my former company Microsoft, Apple and Oracle.
Take a look:
Here they are, a little bit larger:
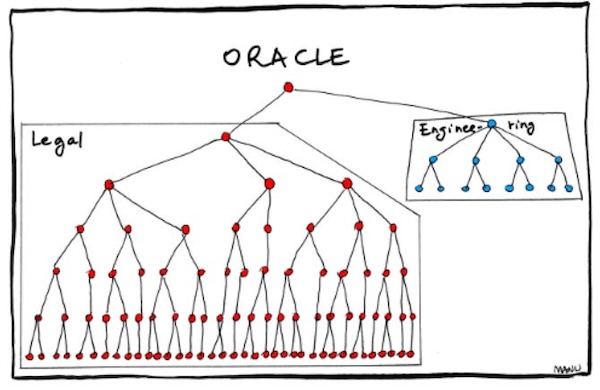
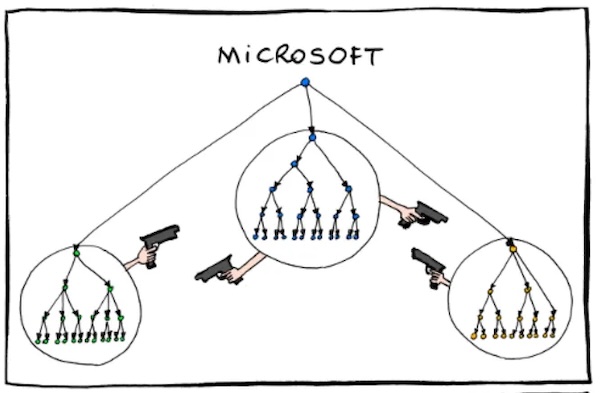
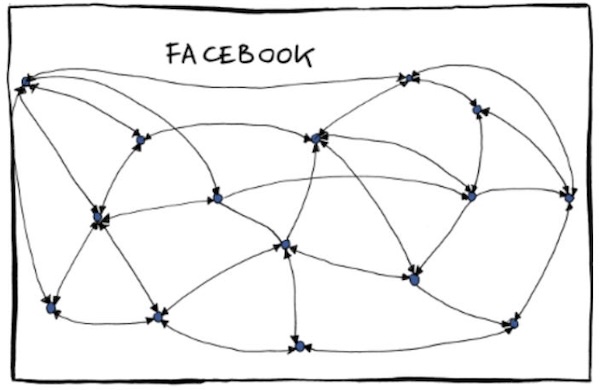
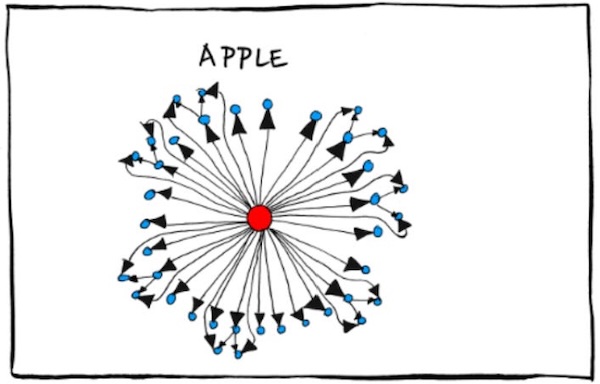
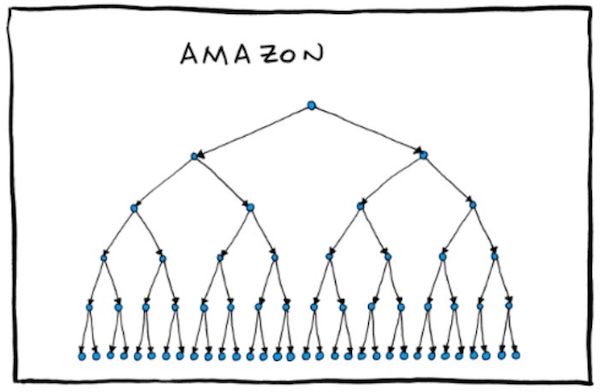
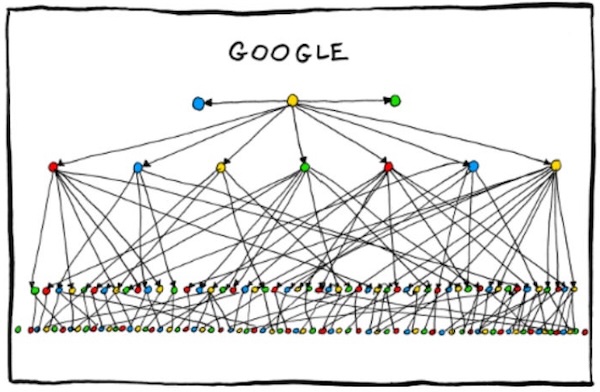
This weekend, someone showed me the org charts and asked me how true-to-life the Microsoft org chart was. I told him “It’s a satire piece, and as such, they’re going to take some liberties with the truth for comic effect. I’d have drawn it like this…”
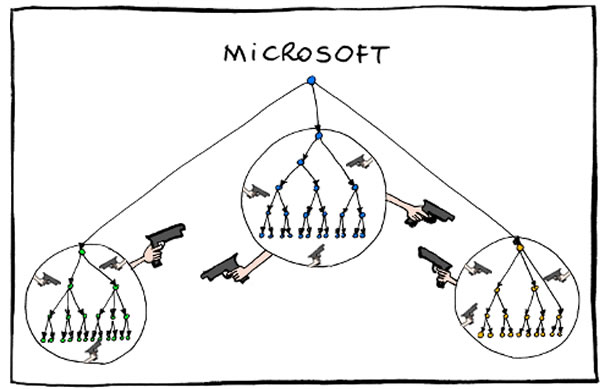
I kid because I love.

Okay, now I’m ready to hit the streets.
This article also appears in The Adventures of Accordion Guy in the 21st Century.
Robert Morris was the cryptographer’s cryptographer. A compiler developer and contributor to Unix at Bell Labs, he developed the password encryption scheme for authenticating users, the direct descendants of which are still in use today. He also wrote the program we know and love as crypt as well as the math library. He went on to work for the government, including decoding encrypted evidence for the FBI and planning cyberattacks on Iraq’s command-and-control systems in the first Gulf War.
You may be forgiven for mistaking him for his similarly-named son, Robert Tappan Morris, who gained notoriety for accidentally creating the Morris Worm. He’s since received a Ph.D. at Harvard, became a member of the faculty at M.I.T. and is often one of the people who vets Paul “Y Combinator” Graham’s essays before he posts them online.
Morris strikes me as the sort of character whom you might read about in a William Gibson or Neal Stephenson novel. He even has a quote worthy of appearing in a book written by either novelist:
The three golden rules to ensure computer security are: do not own a computer; do not power it on; and do not use it.
Morris died last Sunday at home in Lebanon, New Hampshire at the age of 78. Requiescat in pace, Mr. Morris; I’ll be toasting you at the pub later this afternoon.
This article also appears in the Shopify Technology Blog.